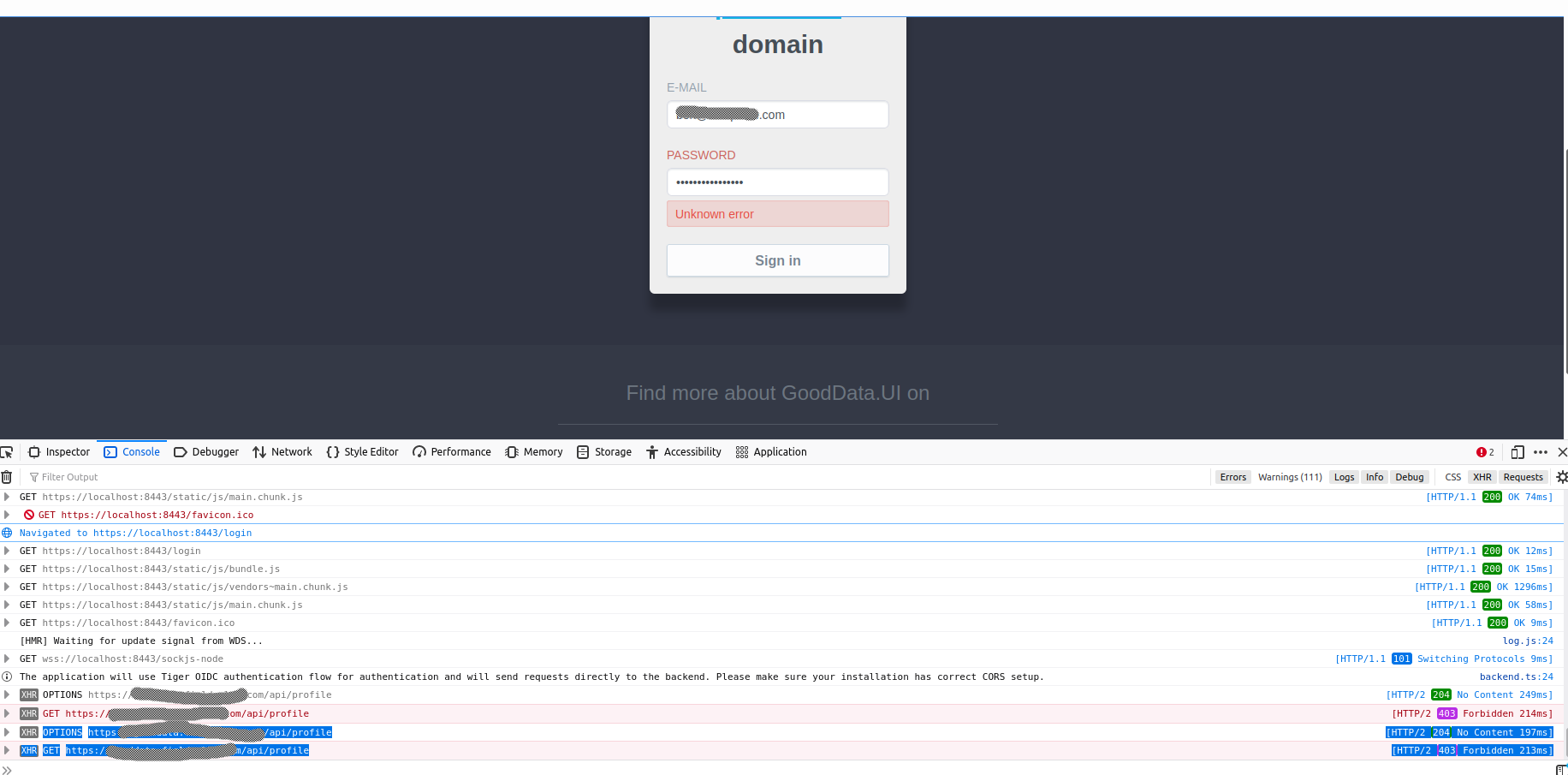
Hello,
We have configured CORS by using the following Ingress options:
apiVersion: networking.k8s.io/v1
kind: Ingress
metadata:
annotations:
meta.helm.sh/release-name: gooddata-cn
meta.helm.sh/release-namespace: gooddata-cn
nginx.ingress.kubernetes.io/cors-allow-headers: X-GDC-JS-SDK-COMP, X-GDC-JS-SDK-COMP-PROPS,
X-GDC-JS-PACKAGE, X-GDC-JS-PACKAGE-VERSION, x-requested-with, X-GDC-VALIDATE-RELATIONS,
DNT, X-CustomHeader, Keep-Alive, User-Agent, X-Requested-With, If-Modified-Since,
Cache-Control, Content-Type, Authorization
nginx.ingress.kubernetes.io/cors-allow-origin: example.com
nginx.ingress.kubernetes.io/enable-cors: "true"
creationTimestamp: "2022-03-28T12:58:20Z"
generation: 4
labels:
app.kubernetes.io/component: dex
app.kubernetes.io/instance: gooddata-cn
app.kubernetes.io/managed-by: Helm
app.kubernetes.io/name: gooddata-cn
app.kubernetes.io/version: 1.7.1
helm.sh/chart: gooddata-cn-1.7.1
name: gooddata-cn-dex
namespace: gooddata-cn
resourceVersion: "83817680"
uid: e0546e76-2c33-49a0-a2c4-e8a17a609605
However, when doing GET or OPTIONS requests at https://example.com/api/profile the Access-Control-Allow-Origin header is always set to “*”.
Are we doing something wrong?
Best answer by Ulku Kijasev
View original